Secure your critical infrastructure with Civintec's robust data center access control. Prevent unauthorized access, enforce anti-passback, role-based control, and real-time monitoring.
 Share
Share Download
Download
In modern data centers, access control is as important as network security, it isn’t just about doors but also about ensure the right people access the right areas at the right time. To handle the challenges such as unauthorized entry, tailgating entry, shared credentials, the combination of CT9 terminal and Cidron reader delivers a powerful solution designed to meet the highest standards of security in data centers, every entry and exit must be authorized, monitored, and recorded with anti-passback access control.

In data centers, unauthorized entry like reader tampering, credential colone, lending or tailgating can lead to serious risk.
CT9 terminal enforce anti-passback logic at hardware level, ensures users cannot re-enter without properly exiting first, preventing badge sharing and tailgating.
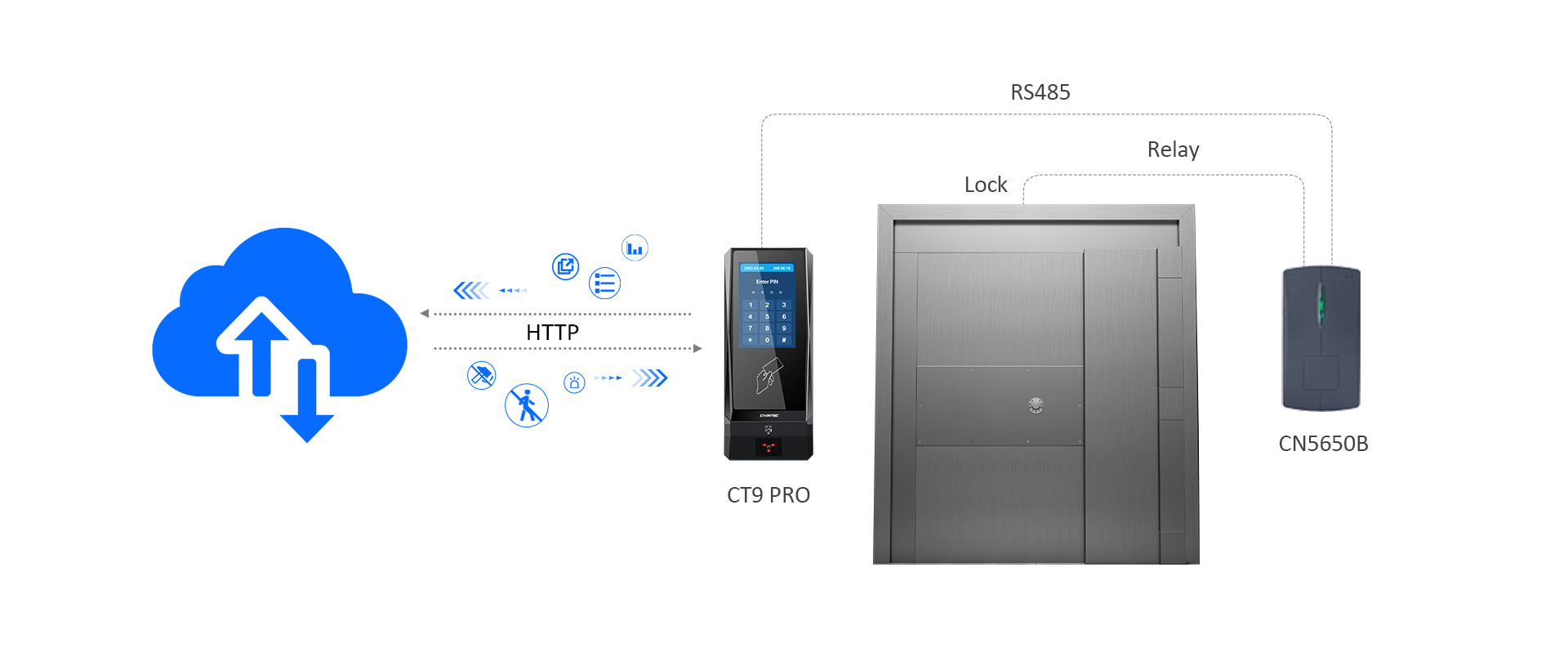
CT9 terminal support wiegand input to work with Cidron reader for both exit and entrance access control.
Both CT9 and Cidron reader support high-security encrypted cards such as Mifare, Mifare Plus, DESFire EV1/EV2/EV3 and AV1/AV2/AV3 with DES/3DES/AES encryption, preventing card cloning or duplication.
CT9 terminal enforce anti-passback logic at hardware level, ensures users cannot re-enter without properly exiting first, preventing badge sharing and tailgating.
This system offer multiple technologies credentials combined with dynamic door-opening password to prevent card colone, credential lending or unknown entry, ensuring that only authorized individuals with verified credentials can enter.
Shared data centers require different levels of access with limited time or area permissions for different people such as visitors, tenants, maintenance staff.
CT9 terminal supports 2 factors authentication (2FA), combining RFID/QR code/mobile credential with dynamically generated real-time PIN code. This dual-layer verification ensures heightened security by requiring both physical credentials and a time-sensitive digital code for access.
Administrators can remotely and centrally manage cross-regional access permissions for multiple enterprises via the management system. Access rights are assigned based on user roles and designated zones, ensuring personnel can only enter areas relevant to their responsibilities.
The system enables time-restricted access, allowing authorization only during predefined hours. This automated approach minimizes manual permission management while maintaining rigorous access control.
maintenance). This automated approach minimizes manual permission management while maintaining rigorous access control."
Our role-based access system minimizes human error and prevents misuse by automatically restricting each user's access - both by location and time - to only what their role requires.
Lack of real-time monitoring capabilities and delayed incident response mechanisms can lead to security failure and inefficient administration.
With wire and wireless TCP/IP, Wi-Fi and 4G, CT9 terminal support online HTTP/HTTPs communicaiton protocol to work with remote cloud management software for real-time data transmission. Administrators are able to remotely control door lock and simultaneously monitor access status in real-time on cloud-based management systems.
CT9 terminal supports multiple alarm outputs that trigger instantaneously upon system detection of tampering, unauthorized access attempts, door-forced-open events or improper door closure ensuring administrators receive real-time notifications for immediate response.
These real-time monitoring systems help administrators maintain full awareness and enable efficient control over operations.
Data centers need full comprehensive traceability for all access events and security incidents.
The CT9 terminal records every access attempt with details including visitors, access authentications, timestamp and logs the data, with
multiple alert output to enable track the forced entry incidents or invalid access attempts and facilitating report export.
Administrators gain full visibility into who entered with what level credentials, when they entered, and how long they stayed, enabling effective monitoring of entries and documentation for review.
This not only supports attendance analysis for technical staff and visitors, but also enables historical security events tracking reports.
Securing data center access demands more than physical door lock control, it requires intelligent control, encrypted authentication, and real-time monitoring. The integrated solution of CT9 terminal and CN5650B reader delivers a comprehensive access control system that prevents unauthorized entry, enforces role-based access, provides real-time monitoring, and maintains a detailed audit trail of every movement for reporting.
Please Contact us and explore a solution with CT9 to secure your data center.